- Community Hub
- Forum Q&A
- Business iQ (Analytics)
- Cisco Cloud Observability
- Controller (SaaS, On Premise)
- Dashboards
- Dynamic Languages (Node.JS, Python, PHP, C/C++, Webserver Agent)
- End User Monitoring (EUM)
- Infrastructure (Server, Network, Database)
- Java (Java Agent, Installation, JVM, and Controller Installation)
- Licensing (including Trial)
- .NET (Agent, Installation)
- Privacy and Security
- Smart Agent
- General Discussions
- Resources
- Groups
- Idea Exchange
Click the Start a free trial link to start a 30-day SaaS trial of our product and join our community as a trial customer. If you are an existing customer do not start a free trial.
AppDynamics customers and established members should click the sign in button to authenticate.
- Cisco AppDynamics Community
- Resources
- Knowledge Base
- How can I configure Microsoft Active Directory Fed...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
12-18-2018
02:56 PM
- edited on
08-26-2019
05:23 PM
by
Claudia.Landiva
You can configure Microsoft Active Directory Federation Services (ADFS) as a SAML authentication provider for the AppDynamics Controller. The instructions below apply to ADFS v2.0, 2.1, and 3.0.
Table of Contents
- Add the Relying Party Trust for AppDynamics Application in ADFS
- Add a Claim Rule
- Pass Group Information in SAML Response
- Download the X509 Certificate for AppDynamics
- Complete the AppDynamics SAML Config for ADFS
- Troubleshooting
Note: After upgrading the Controller to v4.5.x, you may encounter an issue where the SAML authentication request fails for accounts that use Active Directory Federation Services (ADFS) SAML. We suggest you configure your ADFS to send the NameID attribute in the SAML assertion following the steps outlined here: How do I troubleshoot Active Directory Federation Services (ADFS) SAML?
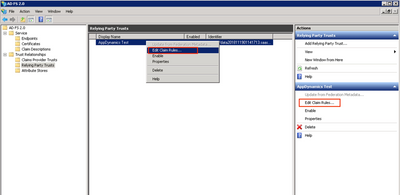
Add the Relying Party Trust for AppDynamics Application in ADFS
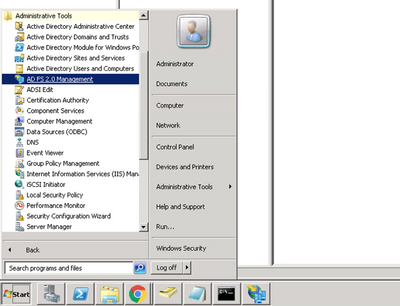
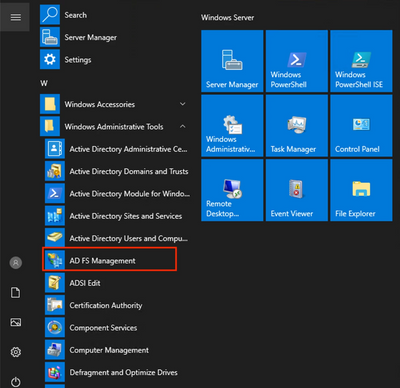
Step 1. Open AD FS 2.0 by clicking Management Start → Administrative Tools → AD FS 2.0 Management.
There is a slightly different workflow depending on your version of Windows Server. Earlier versions require an intermediate step.
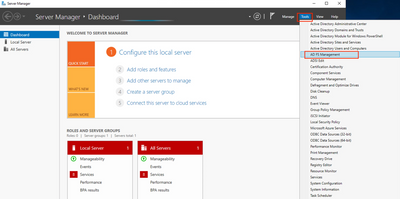
Windows Server 2012 or later
If you are using Windows Server 2012 or above, reference the screenshots below. Then, skip to Step 3 - Add Relying Party Trust.
Windows Server 2008 or earlier
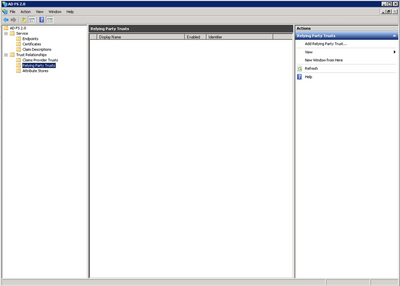
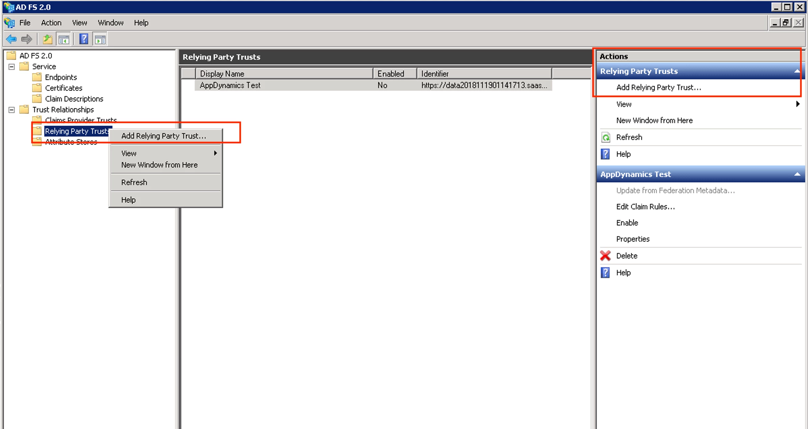
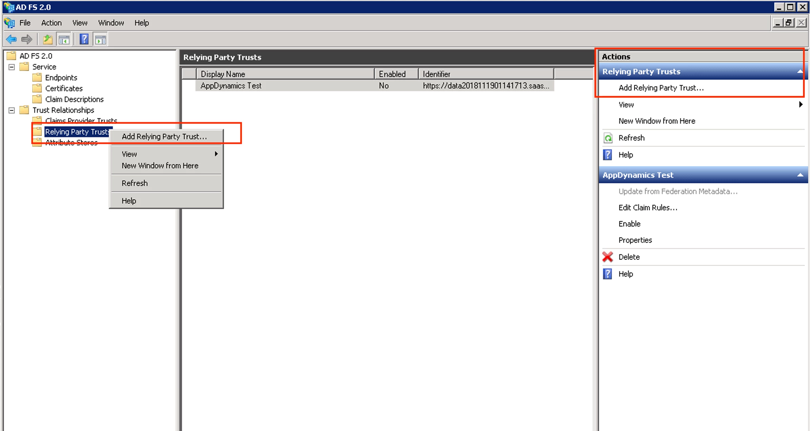
Step 2. For Windows Server 2008 or earlier only: Expand Trust Relationships → Relying Party Trusts.
Step 3. Add a Relying Party Trust. The steps depend on the version of Windows Server you are on. Click below for the instructions that fit your context.
Windows Server 2008 and earlier
1. Trust Relationships → Right click on Relying Party Trusts → Add Relying Party Trust
Windows Server 2012 and earlier
1. Trust Relationships → Right click on Relying Party Trusts → Add Relying Party Trust
2. Actions → Relying Party Trusts → Add Relying Party Trust…
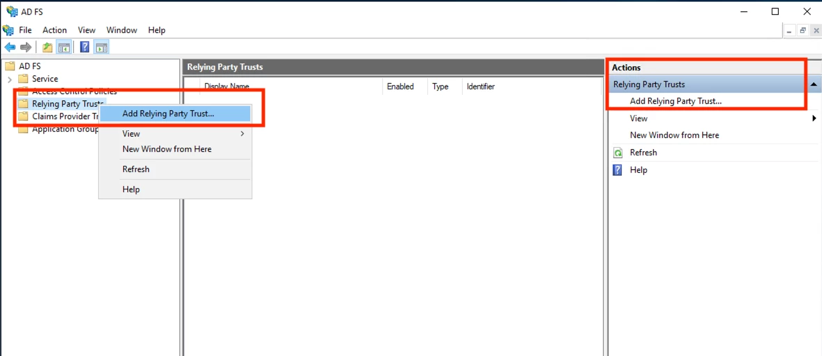
Windows Server 2012 and later
1. Actions → Relying Party Trusts → Add Relying Party Trust…
2. Right click on Relying Party Trusts → Add Relying Party Trust…
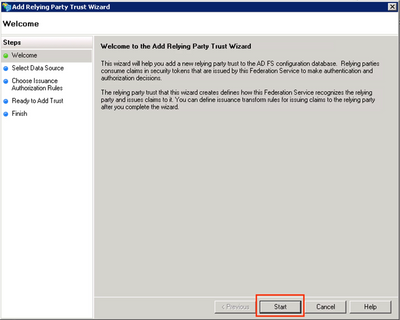
Step 4. Click Start on the Add Relying Party Trust Wizard.
For versions 2016+, select Claims aware → Start.
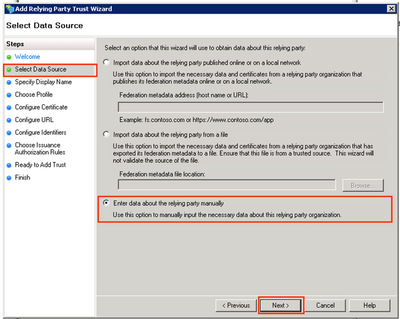
Step 5. On the Select Data Source Page, select the Enter data about the relying party manually option → Next.
Step 6. On the Specify Display Name page, enter Display Name → Next.
Step 7. On the Choose Profile Page (through Windows Srver 2016), select AD FS 2.0 profile → Next.
Note: This step does not exist for ADFS on Windows Server 2016 or later.
Step 8. On the Configure Certificate page, add the certificate if you want to encrypt the SAML response. For details, see Enabling SAML Authentication. Otherwise, click Next.
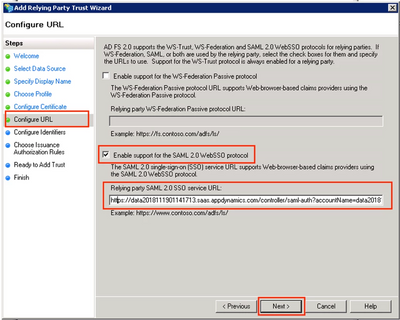
Step 9. On the Configure URL page, check the Enable support for the SAML 2.0 WebSSO protocol checkbox and enter the Relying party SAML 2.0 SSO service URL in the following format. Then click Next.
Format:
http[s]://<controllerurl>:<port (if any)>/controller/saml-auth?accountName=<accountName>
Example:
https://data20181119011417134.saas.appdynamics.com/controller/saml-auth?accountName=data20181119011417134
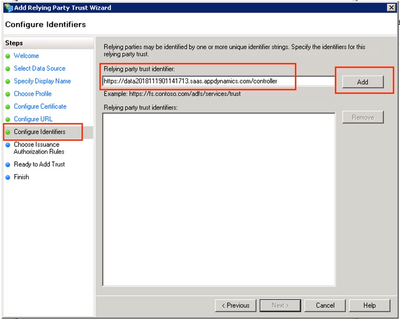
Step 10. On the Configure Identifiers page, enter the Relying Trust Identifier in the following format.
Click Add → Next.
Format: http[s]://<controllerurl>:<port (if any)>/controller
Example: https://data20181119011417134.saas.appdynamics.com/controller
Step 11. On the Choose Issuance Authorization Rules page, select Permit all users to access this relying party → Next.
Step 12. On the Ready to Add Trust page, click Next.
Step 13. On the Finish page check the Open the Edit Claim Rules dialog for this relying party trust when the wizard closes checkbox → Close.
Add a Claim Rule
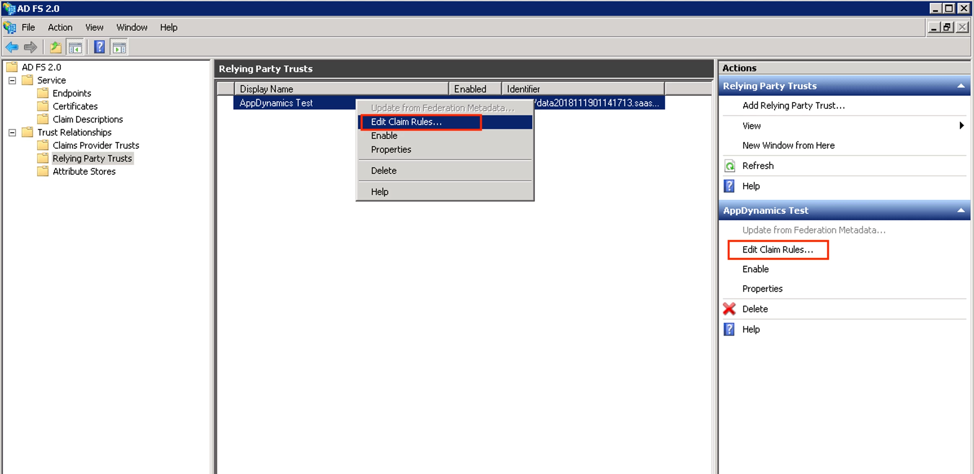
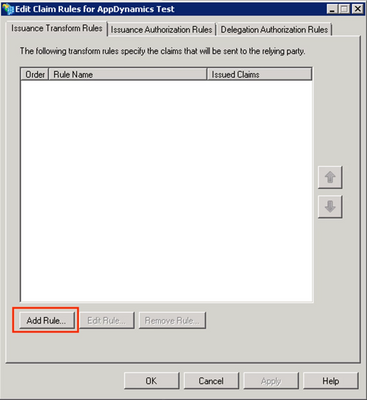
Step 1. Click on Edit Claim Rules... to add the claims.
Step 2. On the Edit Claim Rule page, click Add Rule.
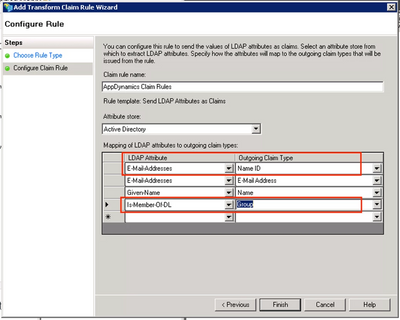
Step 3. The Add Transform Claim Rule Wizard will open. Select Send LDAP Attributes as Claims as the Claim Rule Template → Next.
Step 4. On the Configure Claim Rule page, enter the Claim Rule Name and select Active Directory as Attribute Store. Add LDAP attributes accordingly and click Finish → OK. The Name ID is the required parameter for Controller version 4.5+. Click here for instructions on adding the Name ID.
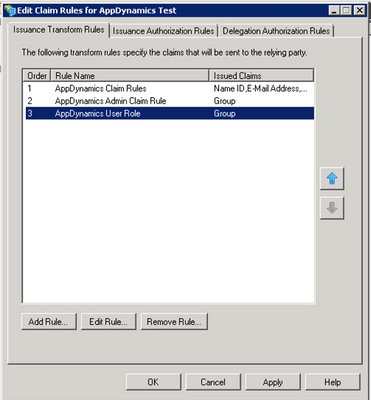
Pass Group Information in SAML Response
There are 2 ways to pass the group in SAML response:
1. Pass the LDAP attribute and map it to the desired group(s) or role(s)
Pass the LDAP attribute Is-Member-Of-DL and map it to Group or Groups or Roles or the name which you like.
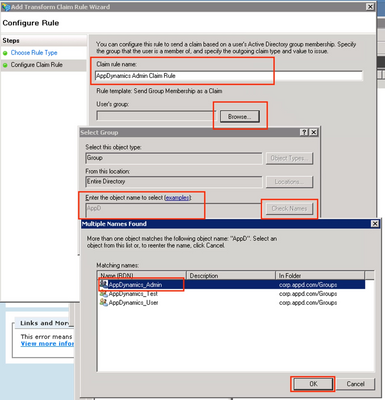
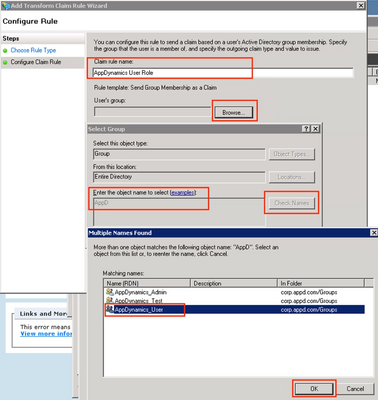
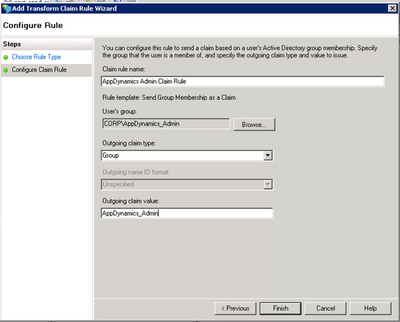
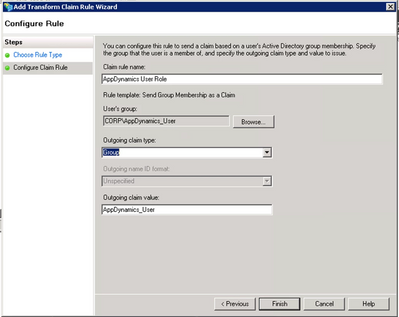
2. Add Groups one by one
Step 1. Click Edit Claim Rules…
Step 2. On the Edit Claim Rules page, click Add Rule.
Step 3. Select Send Group Membership as a Claim as the Claim Rule template → Next.
Add the Desired Group. You have to create a new claim for each group.
Download the X509 Certificate for AppDynamics
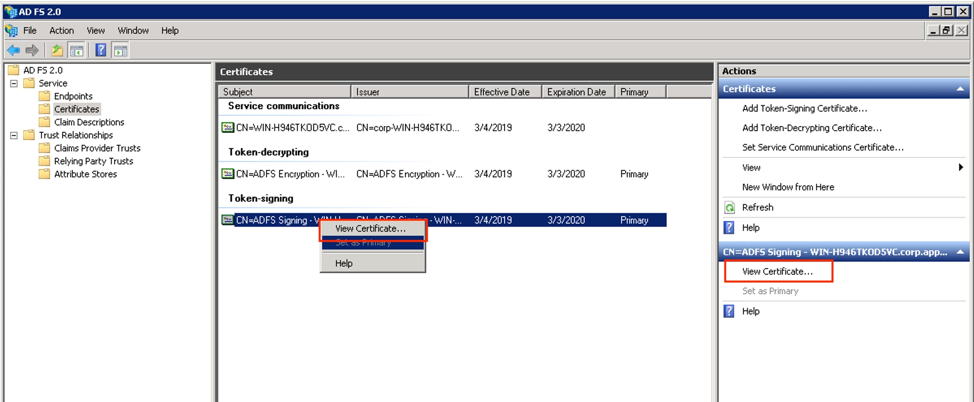
Step 1. Go to the Token Signing Certificate → right-click on the available certificate → View certificate.
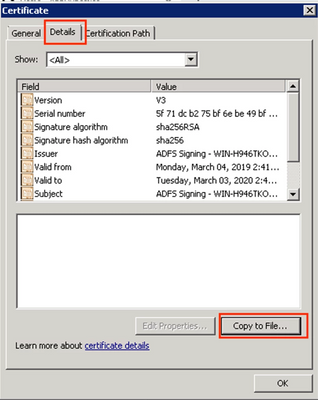
Step 2. On the Details tab, click Copy to File…
Step 3. The Certificate Export Wizard will open. Click Next to begin.
Step 4. Select Base-54 encoded X.509 (.CER) as the format → Next.
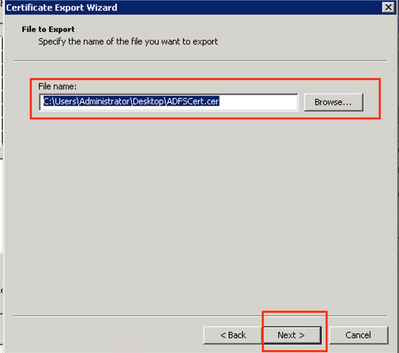
Step 5. Browse to locate the file → Next.
Step 6. Click Finish. You’ll see a notification saying the export was successful.
Complete the AppDynamics SAML Config for ADFS
Follow the steps outlined in our documentation to complete the AppDynamics SAML config: Enabling SAML Authentication.
Troubleshooting
Configure the Time Skew for Active Directory Federation Services
If the system time for the Active Directory server and the Controller machine do not align, you can configure the time skew for Active Directory.
To set the time skew, run the following command in PowerShell:
Set-ADFSRelyingPartyTrust -TargetName AppDynamics -NotBeforeSkew <time_in_minutes>
For example, run the following command to set the time skew to 3 minutes:
Set-ADFSRelyingPartyTrust -TargetName AppDynamics -NotBeforeSkew 3
HTTP Controller Endpoint Test
- Depending on your browser, install one of the following tools:
-
Chrome - SAML DevTools extension' 0.6
-
Firefox - SAML-tracer
-
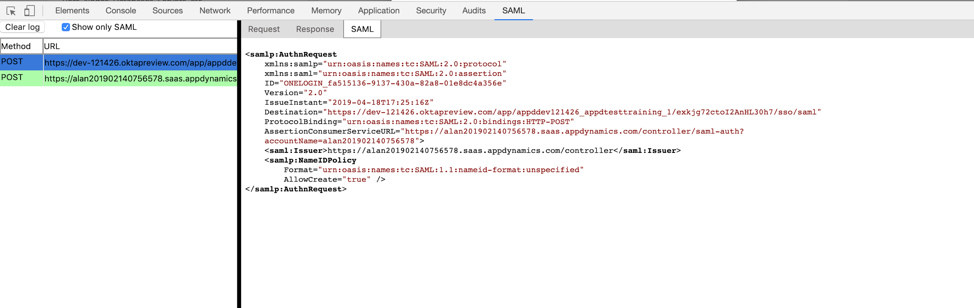
Sign on with the Developer Tools window open.
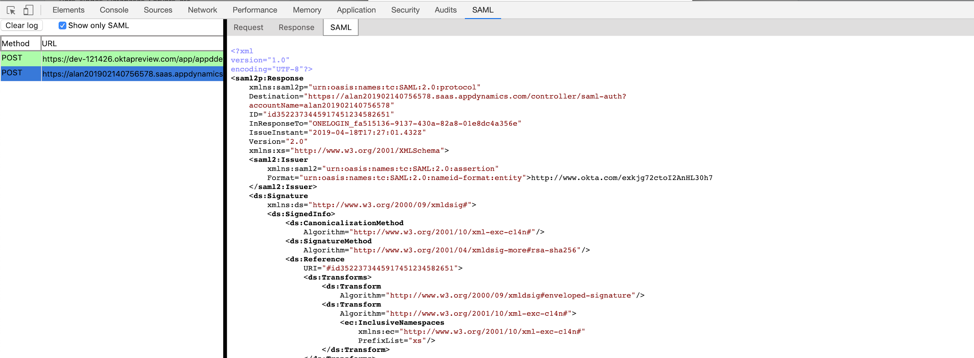
You will see Request and Response as mentioned below
Request:
Response:
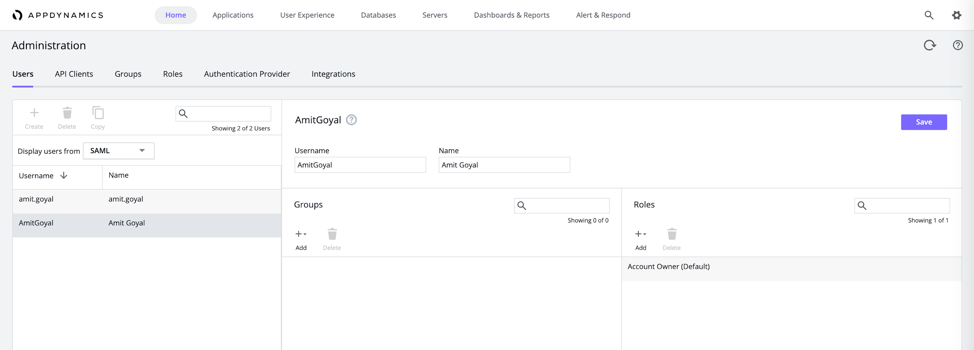
- After successful login, a user will automatically be created with SAML Source in AppDynamics.
- Test the logout process from the Controller.
- The resulting AttributeStatement in the SAML response will be like:
<saml2:AttributeStatement
xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">
<saml2:Attribute
Name="user.email"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<saml2:AttributeValue
xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string">amit.goyal@appdynamics.com
</saml2:AttributeValue>
</saml2:Attribute>
<saml2:Attribute
Name="user.name"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<saml2:AttributeValue
xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string">Amit
</saml2:AttributeValue>
</saml2:Attribute>
<saml2:Attribute
Name="user.login"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<saml2:AttributeValue
xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string">amit.goyal@appdynamics.com
</saml2:AttributeValue>
</saml2:Attribute>
<saml2:Attribute
Name="Groups"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<saml2:AttributeValue
xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string">Appd-Admin/Admin
</saml2:AttributeValue>
<saml2:AttributeValue
xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string">Appd-ReadOnly
</saml2:AttributeValue>
</saml2:Attribute>
</saml2:AttributeStatement>
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for the feedback @Blake.Salvador, I've updated the article.

Thank you! Your submission has been received!
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form