- Community Hub
- Forum Q&A
- Business iQ (Analytics)
- Controller (SaaS, On Premise)
- Dashboards
- Dynamic Languages (Node.JS, Python, PHP, C/C++, Webserver Agent)
- End User Monitoring (EUM)
- Infrastructure (Server, Network, Database)
- Java (Java Agent, Installation, JVM, and Controller Installation)
- Licensing (including Trial)
- .NET (Agent, Installation)
- Smart Agent
- General Discussions
- Resources
- Groups
- Idea Exchange
Not a customer? Click the 'Start a free trial' link to begin a 30-day SaaS trial of our product and to join our community.
Existing Cisco AppDynamics customers should click the 'Sign In' button to authenticate to access the community
- Cisco AppDynamics Community
- Resources
- Knowledge Base
- Configure SAML for Okta
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
At 6pm PST, the AppDynamics Community will go into read-only mode and after migration is complete, you will be redirected to community.splunk.com.
Read more here
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
01-27-2017
12:48 PM
- edited on
12-10-2019
04:53 PM
by
Claudia.Landiva
This topic describes how to configure SAML-based single sign-on (SSO) authentication for Controller access with a particular identity provider, Okta. See SAML Authentication for general information about SAML integration.
How do I configure AppDynamics SAML settings for Okta?
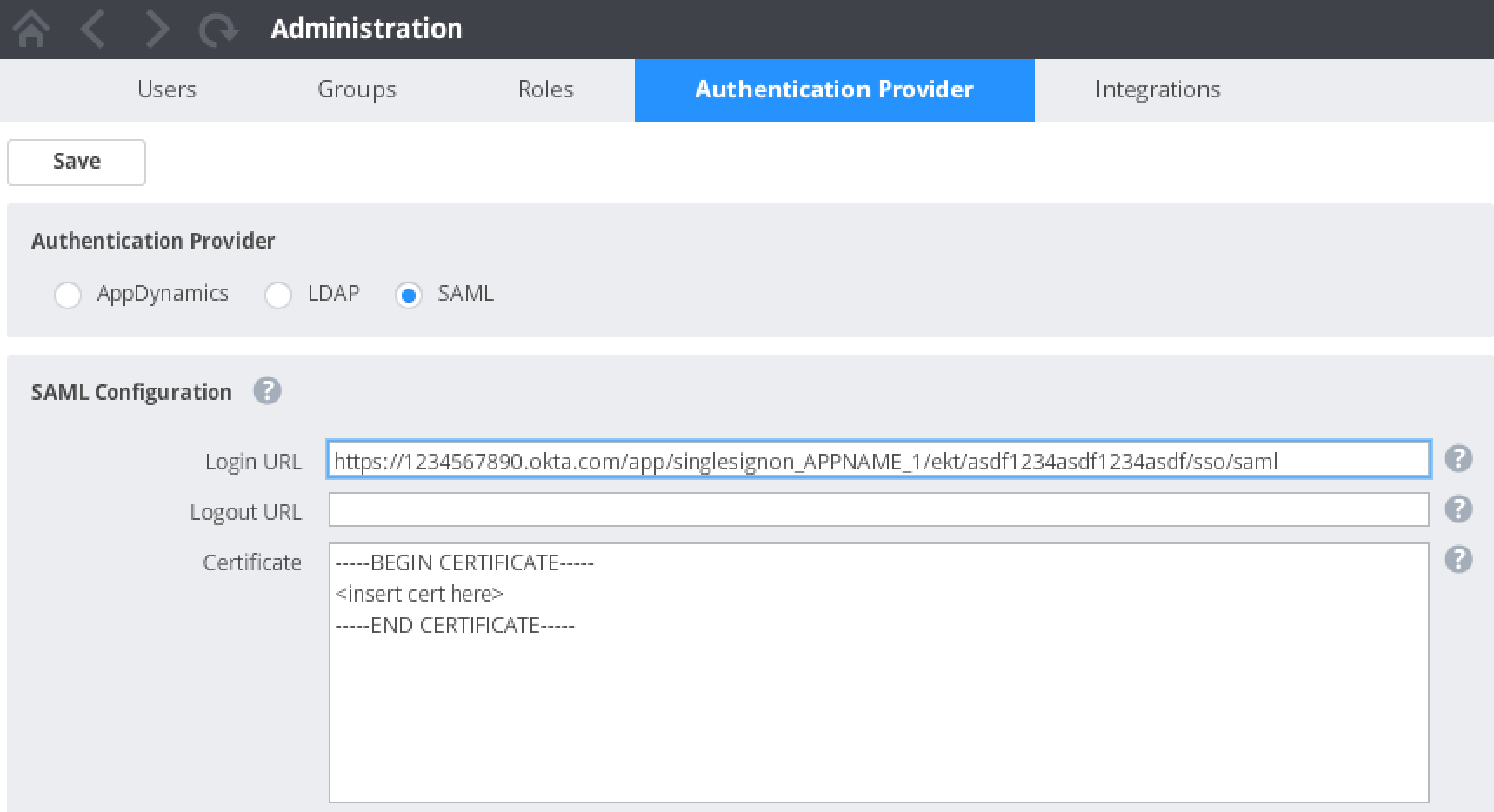
- As an administrator or account owner in the Controller UI, access the Authentication Provider tab in the Administration settings. See SAML Authentication for information.
- Select SAML as the provider.
- In the Login URL field, enter the SAML Login URL from your Okta configuration. The SAML Login URL is the URL to the SSO service at the identity provider. The identity provider provides this URL to the Controller.
If you don't know your SAML Login URL, you can locate it in your Okta configuration:
a. Log in to your Okta account.
b. In the Applications tab, select your application.
c. Click View Setup Instructions.
d. The Identity Provider Single Sign-On URL setting in the Okta configuration is the URL to use for the Login URL in the AppDynamics SAML configuration. - In the Logout URL field in the AppDynamics form, enter the URL to which the browser should redirect when the user logs out. This field is optional. It is used to redirect a user who logs out to an identity provider URL instead of to the AppDynamics login screen. You might want to redirect to the Okta login url.
- In the Certificate field in the AppDynamics form, paste the x.509 certificate from your Okta configuration between the BEGIN CERTIFICATE and END CERTIFICATE delimiters. Do not copy the BEGIN CERTIFICATE and END CERTIFICATE from the SAML x.509 certificate field.
To find your x.509 certificate in your Okta configuration, follow the Setup Instructions referenced above in Step 3. and scroll down to the x.509 Certificate. - In the Default Roles section in the AppDynamics form, select the roles to grant to new users of the SAML-enabled controller by checking the Member checkbox for the role. You can select multiple roles within the list. See Roles and Permissions for information about roles and permissions.
The roles that you assign here will be granted to new users when they first log in to the SAML-enabled controller if those users have not been previously created directly in the Controller. Users created prior to SAML enablement retain their original roles.
You must grant at least one default role. - Click Save.
Configure Okta Settings for AppDynamics
In your Okta account, configure the SAML SSO for AppDynamics.
- Log in to your Okta account.
- Click the Applications tab.
- Click Add Applications.
- Click Create New App.
- Select SAML 2.0 application.
- Click Create.
- Click General and use the wizard to configure these settings. Leave the rest at their default values.
| Setting | Value | Description |
|---|---|---|
| Single Sign On URL | https://<controller_host>:<port>/controller/saml-auth?accountName=<your_AppD_account_name> | The location where the SAML assertion is sent with an HTTP POST |
| Recipient URL | https://<controller_host>:<port>/controller/saml-auth?accountName=<your_AppD_account_name> | URL of the assertion consumer; use Single Sign On URL |
| Destination URL | https://<controller_host>:<port>/controller/saml-auth?accountName=<your_AppD_account_name> | URL where SAML response and assertion is consumed; use Single Sign On URL |
| Audience Restriction | https://<controller_host>:<port>/controller/saml-auth?accountName=<your_AppD_account_name> | The intended audience of the SAML assertion |
| Default Relay State | https://<controller_host>:<port>/controller/ | A URL in AppDynamics where the user is redirected after successful login |
| Response | Signed | |
| Assertion Signature | Signed | |
| authnContextClassRef | PasswordProtectedTransport | |
| Request Compression | Uncompressed |
For URL values, replace <controller_host> and <port> with the address and primary listening port for the Controller. For a SaaS Controller, the URL would be in the form https://<your_org>.saas.appdynamics.com.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
Can someone please help me understand the four different options listed below for configuring sso:
- Configure SAML for OneLogin.
- Configure SAML for Okta
- Configure SAML MSAD on Azure
- Configure SAML for MSADFS
Are all of these options free or do any of this require the purchase of software. Also, I didn't see any documentation for configuring AppDynamics SSO on a Linux application server. We have AD here. Also, is this for SAML 2.0.
Thanks,
Alicia
Join us on Feb 26 to explore Splunk AppDynamics deployment strategies, SaaS models, agent rollout plans, and expert best practices.
Register Now
Dive into our Community Blog for the Latest Insights and Updates!
Read the blog here

Thank you! Your submission has been received!
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form