- Community Hub
- Forum Q&A
- Business iQ (Analytics)
- Controller (SaaS, On Premise)
- Dashboards
- Dynamic Languages (Node.JS, Python, PHP, C/C++, Webserver Agent)
- End User Monitoring (EUM)
- Infrastructure (Server, Network, Database)
- Java (Java Agent, Installation, JVM, and Controller Installation)
- Licensing (including Trial)
- .NET (Agent, Installation)
- Smart Agent
- General Discussions
- Resources
- Groups
- Idea Exchange
Not a customer? Click the 'Start a free trial' link to begin a 30-day SaaS trial of our product and to join our community.
Existing Cisco AppDynamics customers should click the 'Sign In' button to authenticate to access the community
- Cisco AppDynamics Community
- Resources
- Knowledge Base
- How do I use AppDynamics with Cisco Secure Applica...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
12-15-2021
12:38 PM
- edited on
12-06-2022
10:19 AM
by
Claudia.Landiva
Watch this page for updates | Click the 3-dot menu upper right, then Subscribe
We will further update this guidance as we continue to learn from our investigation.
Revised December 23, 2021
How do I find vulnerabilities such as Apache Log4j and block exploits using AppDynamics with Cisco Secure Application?
On December 9, 2021, a vulnerability CVE-2021-44228 in the Apache Log4j Java logging library was disclosed, which could result in remote code execution. On December 14, 2021, another Log4j vulnerability CVE-2021-45046 was disclosed, which could result in a denial of service. CVE-2021-45105, affecting Java 8 and higher environments, was released on December 17.
As an immediate response, the AppDynamics team confirmed the capabilities of Cisco Secure Application to help our customers investigate these Log4j related vulnerabilities, detect them, and block exploits.
Following, we will cover how our customers using Cisco Secure Application can:
- Identify whether you’re using a vulnerable version of Log4j
- Block exploits of the vulnerability
- Determine whether the vulnerability has been exploited
In this article...
- What distinguishes Cisco Secure Application?
- How do I find vulnerabilities using AppDynamics and Cisco Secure Application?
- How do I identify the location of vulnerabilities using discovered libraries?
- How do I configure a policy to block exploits?
- How do I confirm my new policy won't be superseded by an existing one?
- How do I know I've been attacked?
- Additional resources
What distinguishes Cisco Secure Application?
Cisco Secure Application is uniquely capable of enforcing a single policy across all applications that blocks vulnerable Java classes from establishing any network connection regardless of the application interface with negligible performance impacts and is impervious to obfuscation.
It does this all with the operational benefit of being integrated into the AppDynamics APM Java Agent to provide simplified deployment and code-level application context. This combination of ease of use, precision, and performance is an essential addition to a defense-in-depth strategy to protect your applications in production.
How do I find vulnerabilities using AppDynamics with Cisco Secure Application?
NOTE | In order to use AppDynamics with Cisco Secure Application to protect your applications, ensure that all steps from the Getting Started documentation are completed.
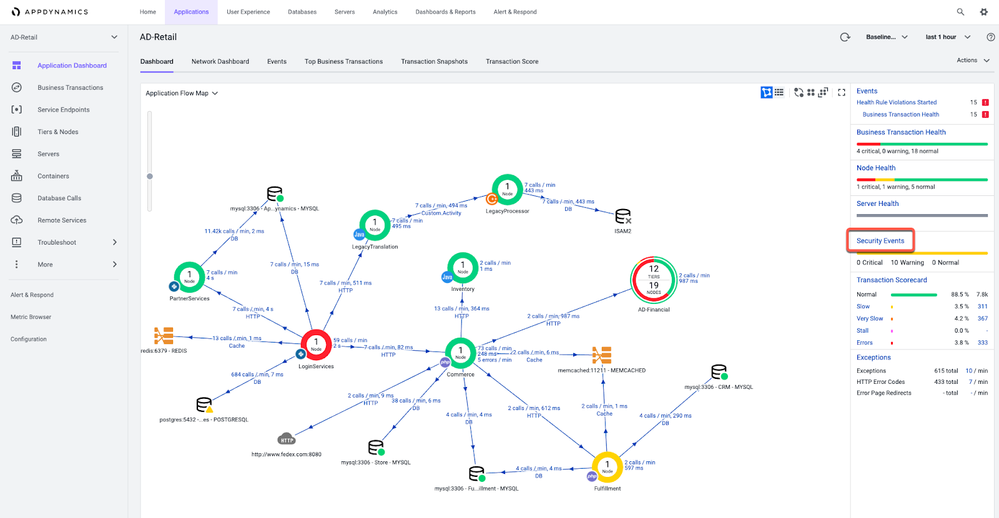
- Access Cisco Secure Application through an AppDynamics Dashboard by clicking on the Security Events link on the right panel.
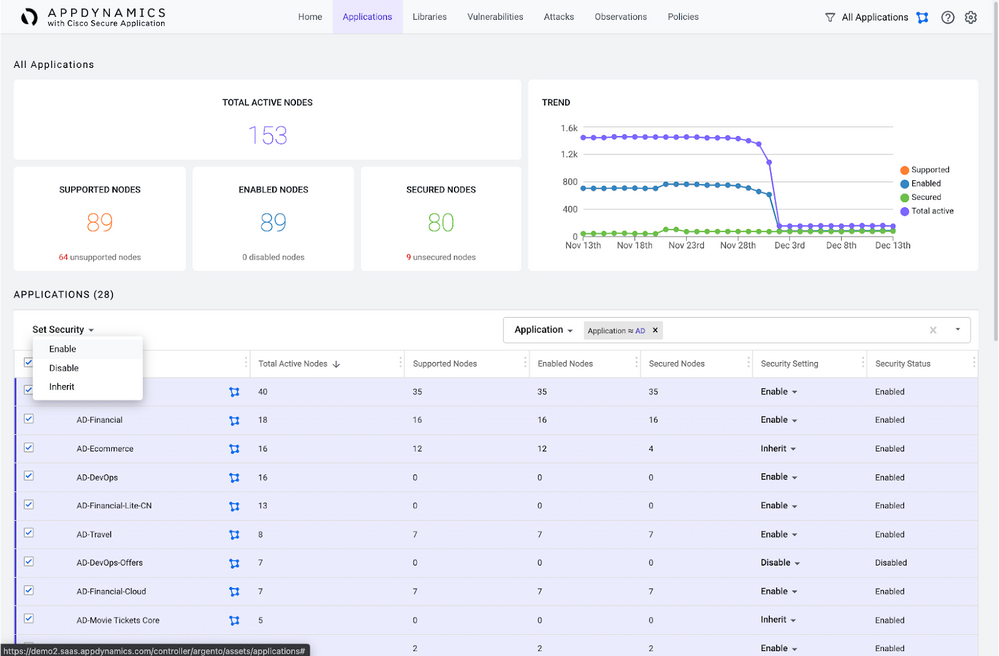
- See which applications are being monitored by selecting Enabled from the Set Security drop-down.
- Click the Vulnerability link to open the Vulnerabilities page.
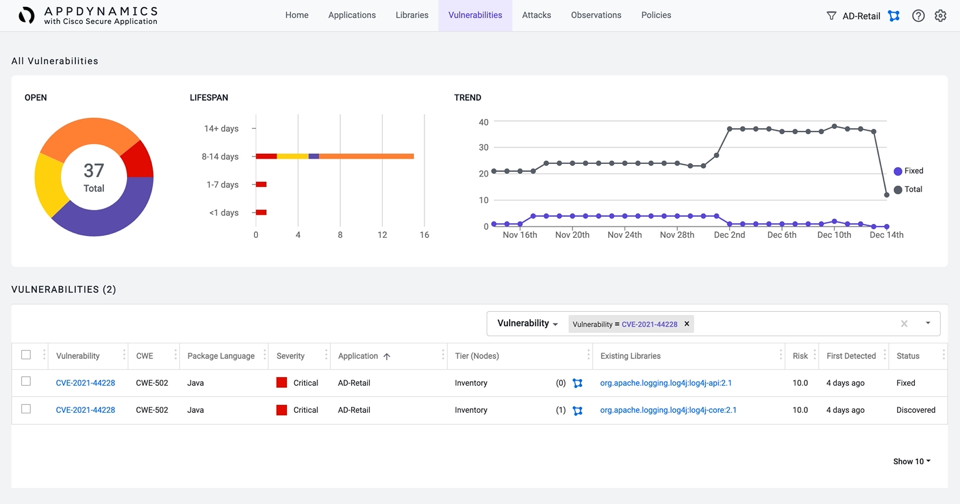
- Find the search bar under the Vulnerabilities list on the lower part of the screen. Choose Vulnerability from the drop-down, then enter the name of the vulnerability.
NOTE | In this example, we used the CVE-2021-44228, otherwise known as the Apache Log4j2 JNDI vulnerability, where malicious individuals can backdoor-execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled (which was the default.)
Please refer to the Apache Security Vulnerabilities page for more details. https://logging.apache.org/log4j/2.x/security.html
- The search results provide an indication of which applications are using the Log4j library. You will also notice that Cisco Secure Application not only knows the severity but knows the CVSS score as well.
In the case of CVE-2021-44228, the CVSS score is 10, which is Critical.
How do I identify the location of vulnerabilities using discovered libraries?
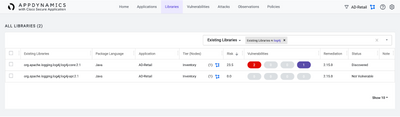
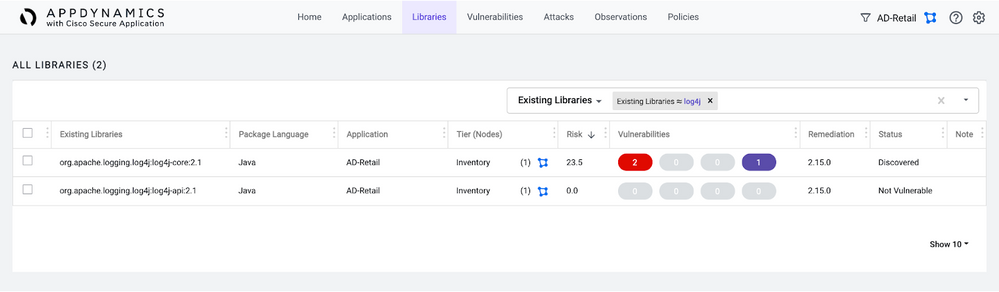
Another way to view and determine where vulnerabilities lie is by looking at global libraries. Here we’ve looked for which libraries contain Log4j.
- Go to the Libraries tab and search Existing Libraries for Log4j.
- In this view of Cisco Secure Application, you can:
- Detect the instances where a vulnerability exists, including the number of instances, and the risk calculation.
-
See indication of remediation, which in the CVE-2021-44228 example is the 2.15.0 version of Log4j. However, remediation of CVE-2021-45046 requires 2.16.0.
- View greater detail by clicking on the particular vulnerability, the severity, date of detection, a clear description with references, all the applications and their corresponding tiers affected, as well as the status.
Cisco Secure Application also provides a reference link to the source from where Cisco Secure Application is getting these details. Just click the redirect link next to the title.
How do I configure a policy to block exploits?
Now that we have identified the vulnerability and affected libraries, as well as the status, we must create a policy to further protect any new application or use of the library in our environment.
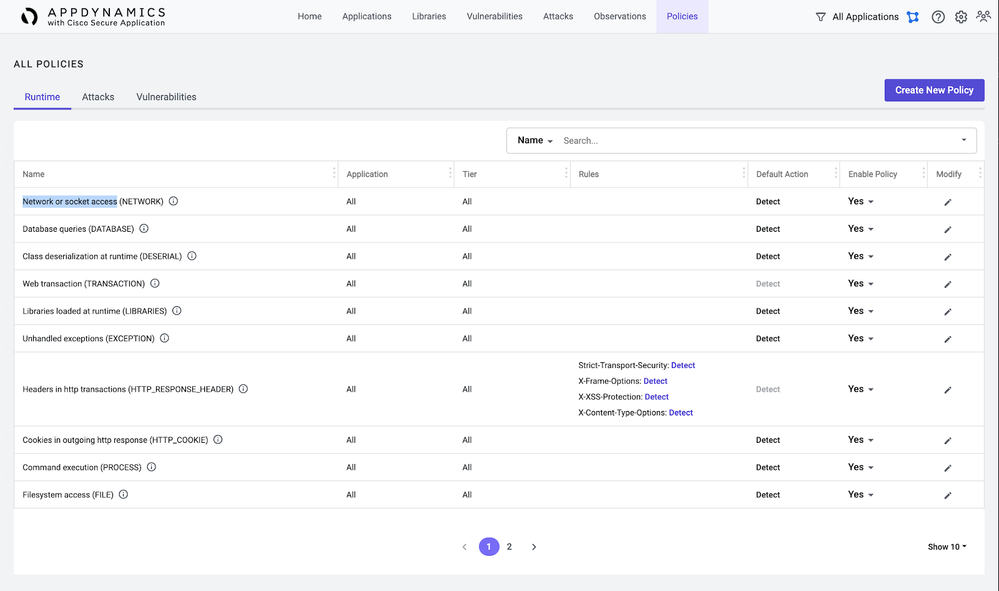
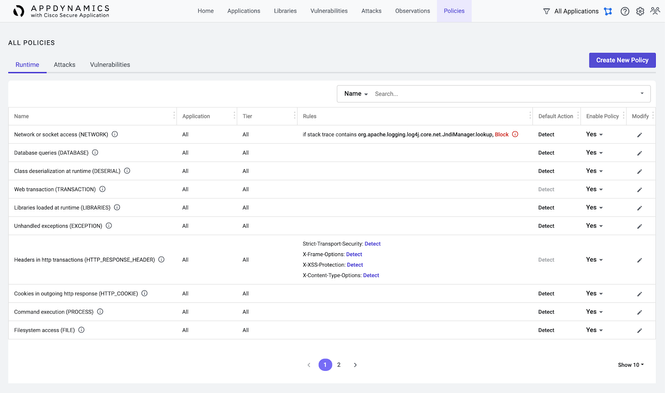
- To begin, click the Policies page. Look for an existing Network or socket access (NETWORK) policy.
If one already exists, click the Modify icon next to the policy for Application All and Tier All. Otherwise, click on Create New Policy.
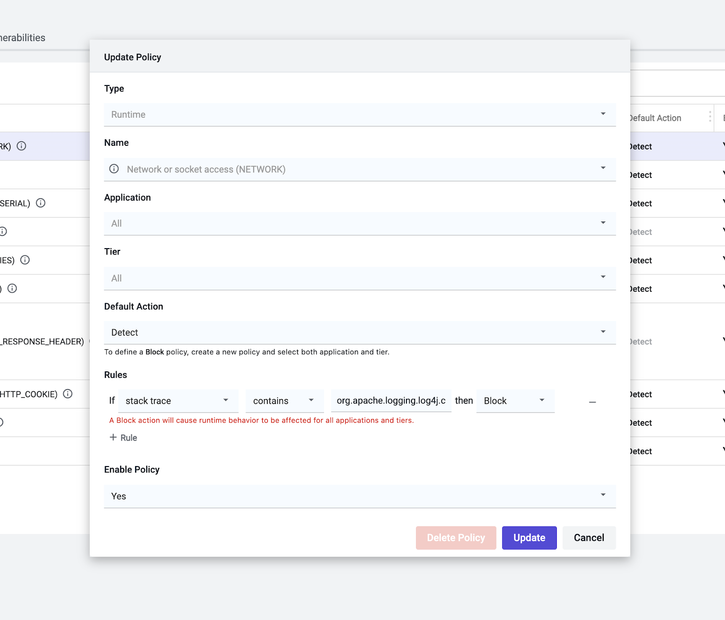
If this is a new policy, select Network or socket access name, and continue with the following steps for updating existing policies. - Within the Rules section, click + Rule and match the rule text below:
For example, your rule could be:
if stack trace contains org.apache.logging.log4j.core.net.JndiManager.lookup, then Block
Then click either Save or Update, depending on whether this is a new or existing policy.
NOTE | The action that you specify within the rule supersedes the default action specified in Default Action.
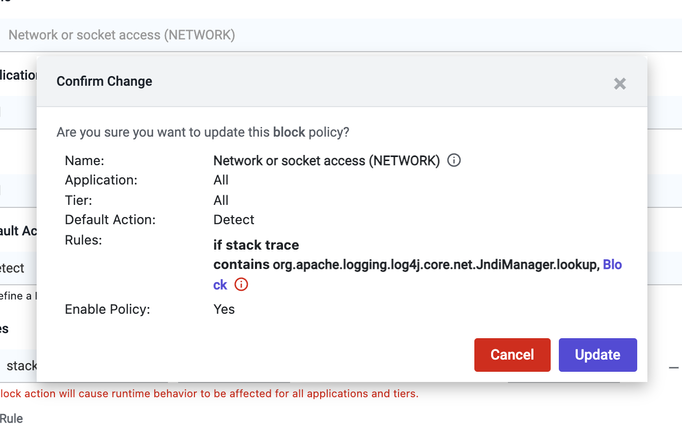
- When presented with the Confirm Change dialog, review the policy to ensure it matches the following settings.
Name Network or socket access (NETWORK) Application All Tier All Default Action Detect Rules If stack trace contains org.apache.logging.log4j.core.net.JndiManager.lookup, then Block Enable Policy Yes
- Once you save the policy, changes will be reflected on the Policies page. Typically, this updated policy will be enforced in the Cisco Secure Application agent in less than five minutes.
How do I confirm my new policy won't be superseded by an existing one?
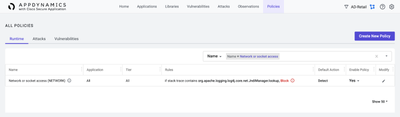
Use the Search filter to confirm that no other Network or socket access policies exist which would supersede the newly defined policy.
- Within the Search filter, select the Name search category from the dropdown list.
- Click the Search field and type Network or socket access, and click Enter.
- If any other Network or socket access policies exist, add rules to each one using the same steps outlined above.
How do I know if I’ve been attacked?
It’s essential to review whether someone exploited this vulnerability, which could lead to them taking complete control of your application and underlying systems. In these steps, you’ll look for exploits of CVE-2021-44228 that resulted in shell command execution. You’ll also search for a blocked attack attempt.
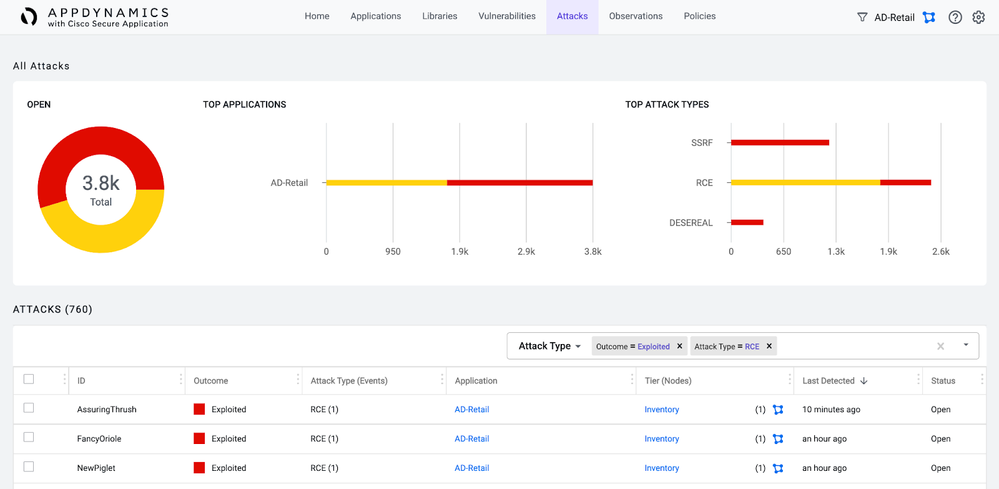
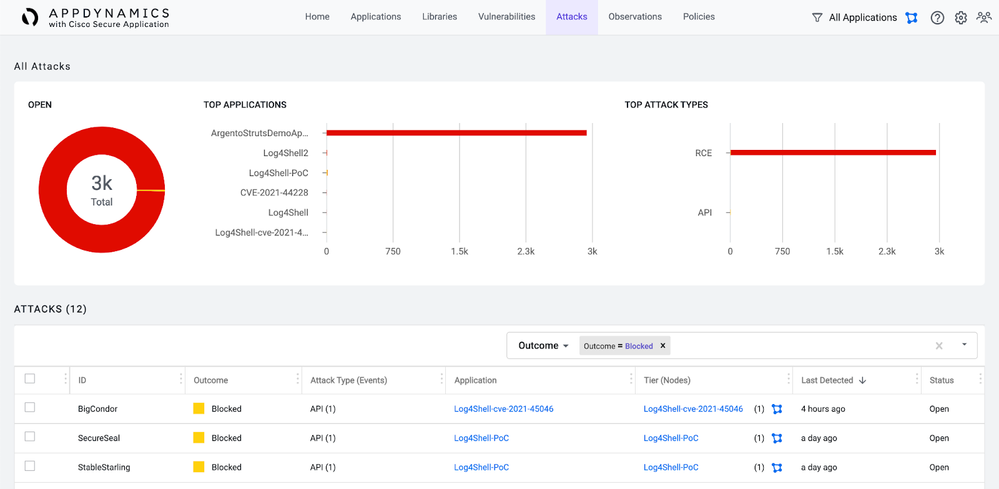
- Go to the Attacks view and search Outcome for Exploited and Attack Type for RCE.
In this view of Cisco Secure Application, you can determine any attacks that resulted in exploitation of a vulnerability and in what Application and Tier it happened. - If you have any attacks with an outcome of Exploited, click within that row to see further details. Within the detailed view, click on the Event with an Outcome of Exploited to view details specific to the events that compromised the attack chain.
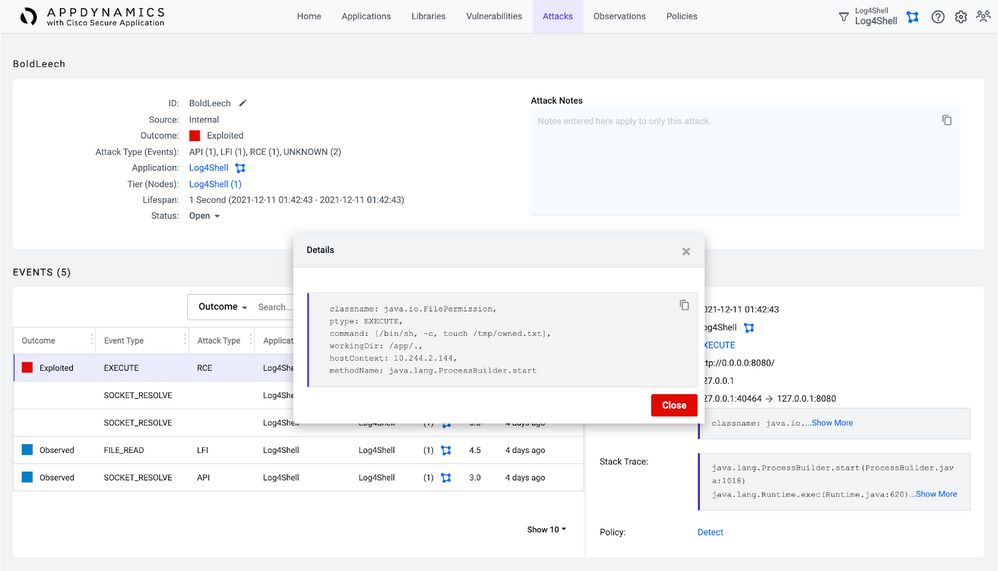
In this view of Cisco Secure Application, you can:
- Determine the specific Node that was exploited, which should now be considered compromised
- See the Client IP where the attack originated. This can be used to do threat hunting across the rest of your applications and infrastructure with a tool like Cisco SecureX
- Capture the socketOut from the event Details to identify the attacker-controlled server your application was instructed to communicate with, which should be used to create filters in your network infrastructure to prevent communication to that host
- Review what shell Command was actually executed and the working directory
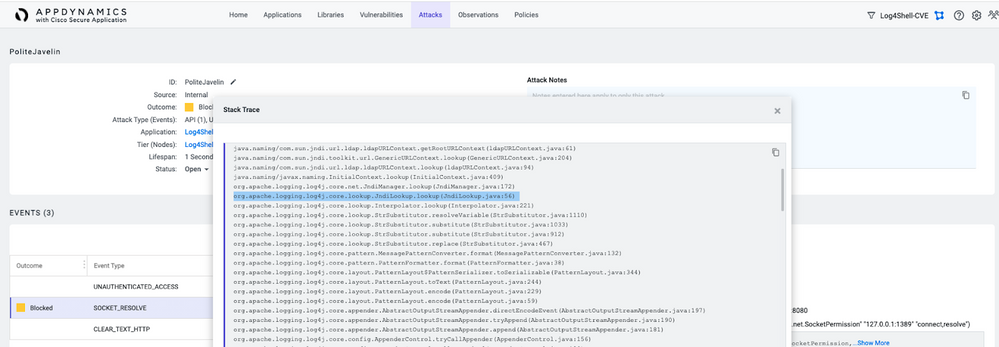
- Confirm that the Stack Trace contains a line with org.apache.logging.log4j.core.net.JndiManager.lookup
- Investigate the Stack Trace to determine where in your code Log4j can be exploited
- Go back to the Attacks view and search Outcome for Blocked. You’re not specifying an Attack Type in the search, because the policy defined earlier stops the attack from making it to that stage in the attack chain.
In this view of Cisco Secure Application, you can determine any attacks that were Blocked and in what Application and Tier it happened. - If you have any attacks with an outcome of Blocked, click within that row to see further details. Within the detailed view, click on the Event with an Outcome of Blocked to view details specific to the events that compromised the attack chain.
In this view of Cisco Secure Application, you can:
- Determine the specific Node that blocked the attack
- Capture the Client IP where the attack originated. This can be sued to do threat hunting across the rest of your applications and infrastructure with a tool like Cisco SecureX
- Capture the socketOut from the event Details to identify the attacker-controlled server your application was instructed to communicate with, which should be used to create filters in your network infrastructure to prevent communication to that host
- Confirm that the Stack Trace contains a line with org.apache.logging.log4j.core.net.JndiManager.lookup
Resources
- AppDynamics Product Investigation and Software Updates:
Security Advisory: Apache Log4j Vulnerability - Cisco Talos Threat Intelligence and Detection: Cisco Talos threat advisory: Critical Apache Log4j vulnerability being exploited in the wild
- AppDynamics Blog:
Log4j vulnerability threat customer response
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Aaron.Schifman has posted a video demo walkthrough of these instructions for using Cisco Secure Application. Check out Defend Log4j Vulnerabilities with Cisco Secure Application on YouTube.
Learn how Splunk and AppDynamics are redefining observability
Register Now!
Dive into our Community Blog for the Latest Insights and Updates!
Read the blog here

Thank you! Your submission has been received!
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form